DAY 16 – Amazon Inspector – Automated and Continual vulnerability management at scale – Day Sixteen

Tweet This Blog – 100 days of Cloud on GitHub – Read On iCTPro.co.nz – Read on Dev.to
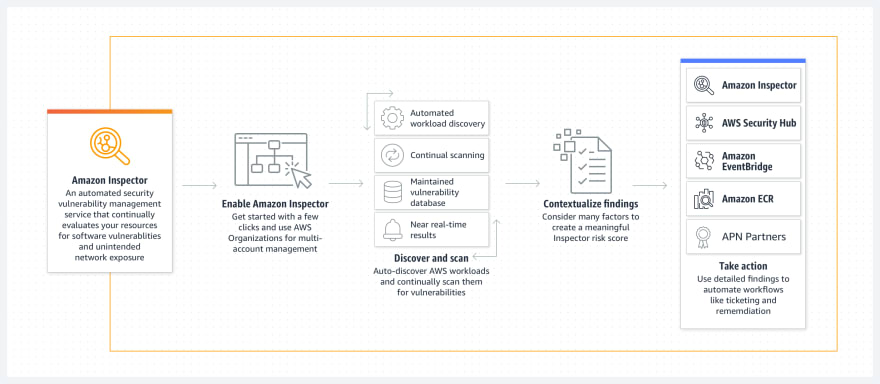
- Quickly discover vulnerabilities
- Prioritize patch remediation
- Meet compliance requirements
- Identify zero-day vulnerabilities sooner
Amazon Inspector helps to find security vulnerabilities on EC2. (Finding Common Vulnerabilities (CVE) , Center of Internet Security Benchmarks (CIS), Security Best practice & run time behavior).
An agent based service, which means you can add agent to your EC2 and start monitoring.
Why Amazon inspector?
- Monitor your application for vulnerabilities
- Crosschecks for Security compliance & exposure to attack.
- Secure your EC2 for zero day vulnerability.
- Low Cost are few of the benefits using Amazon Inspector.
Components
9 components
the Amazon Inspector role, assessment targets, AWS agents, assessment templates, rule packages, assessment runs, telemetry, assessment reports, and findings
🚨 Amazon Inspector role
- A read only access to all your EC2 environment
🎯 Assessment Targets
- A group of Ec2 or target group of Ec2. tags will be used to group.
📦 Agents
Software agents installed on the instance that you wish to monitor (agents are updated automatically). Supports both Linux and Windows.
Installing the Amazon Inspector agent on a Linux
wget https://inspector-agent.amazonaws.com/linux/latest/install
or
curl -O https://inspector-agent.amazonaws.com/linux/latest/install
Then
sudo bash install
For Windows
Download .exe file from this link
or copy paste
https://inspector-agent.amazonaws.com/windows/installer/latest/AWSAgentInstall.exe
and execute AWSAgentInstall.exe
📝 Assessment templates
This will decide how an assignment on ec2 should run. We can use SNS to notify the finding. Once you created you cannot modify the template.
✔️ Rule Packages
Set of individual rules that are checked against EC2 instance with severity level (High, Medium, Low, Informational).
Supported Rules packages
CVE, CIS, Security Best Practices
- CVE – publicly known security threats.
- CIS – Global Standard for Security standards For IT resources
- Security best Practices – Common best practices in Linux based Ec2 targets.
🏃 Assessment Run
Assessment run will be used Once you configure Role, agent, Target & template Configured.
📇 Telemetry
Data collected from instance , once collected the data will be sent to Inspector and stored in s3 with KMS key. Inspector Analyse the data from S3 with rule packages. After 30 days telemetry data is deleted.
📘 Assessment Reports
Provides a assessment on results.
There are Mainly two types of report
- Findings reports
- Summary of assessment
- List of EC2 assessed
- Rules Used
- Findings
- Full report
- all Finding report + List of rules passed successfully for instances
📖 Findings
Results of Assessment run, also gives how to remediate the issues found
Practical
Now Lets install Agent on Debian OS, please refer above to install on Linux
- Lets note down the ec2 tags.
- Goto Amazon Inspector from console and click Get started then Enable Inspector.
- After few minutes you will be welcomed with a dashboard.
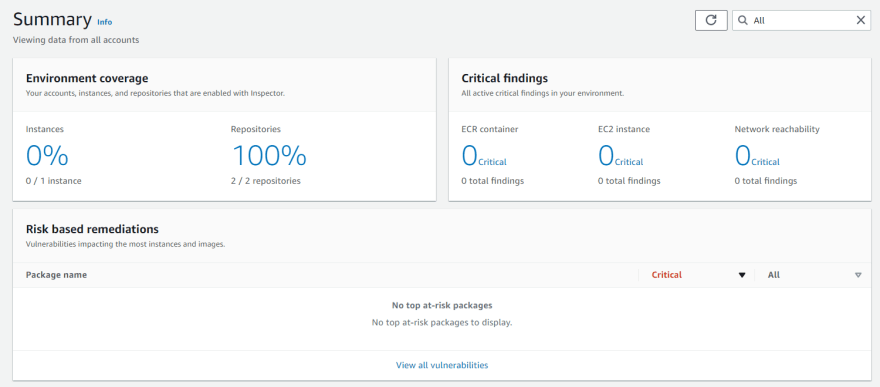
- As you are already installed inspector in will run a default checks.
- If you get confused with new dashboard click on Switch to Inspector Classic

- Click on findings on new dashboard and click the Vulnerability

On bottom of findings you can see how can you remediate the issue.
That’s it , 🎉Congratulations🎉you have successfully implemented AWS inspector for your EC2 infrastructure.
✅Connect with me on Twitter
🤝🏽Connect with me on Linkedin
🧑🏼🤝🧑🏻 Read more post on dev.to or iCTPro.co.nz
💻 Connect with me on GitHub




