DAY 23 – Deploying IAC with your secrets in Terraform Vault – Day Twenty three

100 days of Cloud on GitHub – Read On iCTPro.co.nz – Read on Dev.to
What is Vault?
Securely accesses secrets , HashiCorp explains as Vault comes with various pluggable components called secrets engines and authentication methods allowing you to integrate with external systems. Vault issues temporary tokens to access the resources.
- In the blog I will be demonstrating how to setup a vault
- Accessing secrets from Vault to Deploy your infrastructure into a AWS environment.
Prerequisite
Install AWS CLI and Configure with IAM credentialsGIF

Install Vault
Goto this link to install Vault
I Am using a WSL Linux on windows
- Getting GPG key
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
- Adding HashiCorp Linux repo
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
- install
sudo apt-get update && sudo apt-get install vault
Setup Vault Project folder
- Lets create a project folder named Vault and cd into it
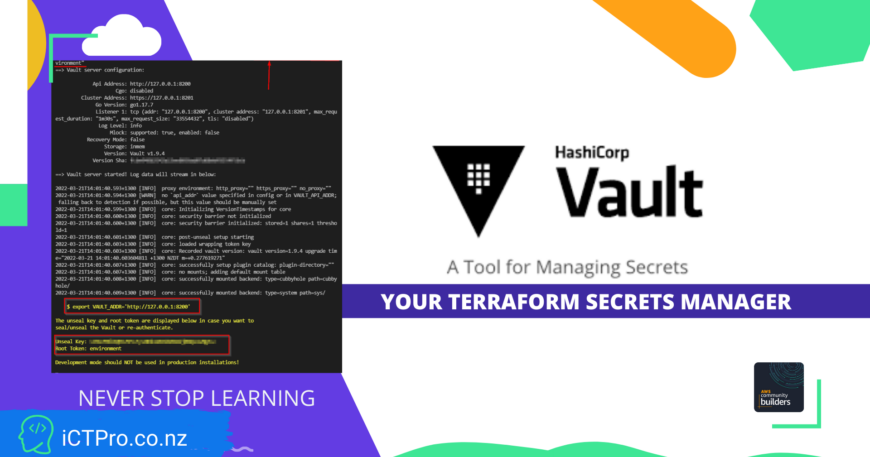
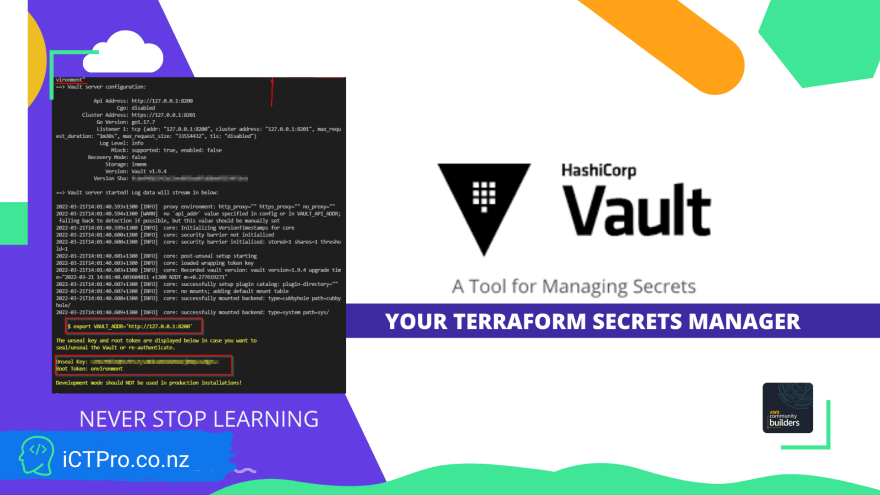
Setup Vault Server (Dev environment)
vault server -dev -dev-root-token-id="environment"

Note down the Vault Address, Unsealkey & Root token.
Sign into vault server
Enter token as “environment”
- Select Secret & Click Create Secret.
- Enter your IAM Programmatic access keys & Save.

Deploying with Vault
- Create a main.tf file and copy paste this command
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "3.58.0"
}
}
}
data "vault_generic_secret" "aws_creds" {
path = "secret/aws"
}
provider "aws" {
region = data.vault_generic_secret.aws_creds.data["region"]
access_key = data.vault_generic_secret.aws_creds.data["aws_access_key_id"]
secret_key = data.vault_generic_secret.aws_creds.data["aws_secret_access_key"]
}
resource "aws_instance" "my_server" {
ami = "ami-059af0b76ba105e7e"
instance_type = "t2.nano"
tags = {
Name = "Vault-Server"
}
}
You have to change ami incase your region is not on ap-southeast-2
- Initialize Terraform
terraform init
- Plan terraform
terraform plan
You will be prompted to enter the vault url, in this case it is http://127.0.0.1:8200/

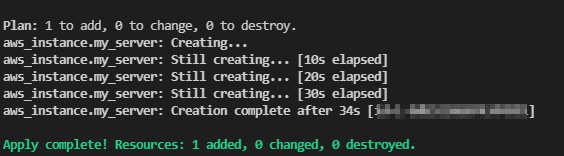
- Deploy infrastructure
terraform apply -auto-approve
- Enter url of vault when its prompted.
- Teardown your infrastructure
if you are happy with the deployment , you can tear down the deployed resources
terraform apply -auto-approve -destroy
😀🎉Congratulations🎉 you have successfully deployed IAC with Terraform VaultGIF

✅Connect with me on Twitter
🤝🏽Connect with me on Linkedin
🧑🏼🤝🧑🏻 Read more post on dev.to or iCTPro.co.nz
💻 Connect with me on GitHub