DAY 30- ISO/IEC 27001 – Day Thirty

100 days of Cloud on GitHub – Read On iCTPro.co.nz – Read on Dev.to
What is ISO/IEC 27000 Series?
A Popular Information Security Management Standard is used to keep your information technology assets secure.
Enabling such standards to help the organization to keep their assets safe such as financial information, intellectual property, employee details, or information entrusted by third parties.
This consists of policies, procedures, guidelines, and resources associated with the organization; which is managed by the organization to protect information assets.
ISO/IEC 27001 is the only standard from ISO27000 families standard that can be audited.
when you define your Risk Assignment and your organization’s risk acceptance will effectively help in treating and managing risks.
ISO/IEC 27001, Information security management systems
- Its important employees commit to ISMS for each company. That will help the employees to understand the obligations and responsibilities that they need to follow, this can achieve by continuous training & reviewing.
- Implement encryptions for your data. Make sure you document everything, log implementation, alarms, etc..
All third party services should be competent about security. - Need to consider any law that can affect your process, this could be like intellectual property laws, this will be different to each country.
- Again, Document everything processes, plans, incident responses, vendors, expected risks etc…
- Confidentiality-Integrity-Availability is the core of information security.
A small challenge for you
What does the below equation proves ?
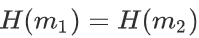
Comment the answer __________________________
What are the factors that influence your Organisation on implementing ISO 27001?
a) Internal
Employees, Owners
b) External
Suppliers, Govt, Regulators, Shareholders etc..
c) Leadership Team
This team Helps in creating an information security Plan. Allocate roles and responsibilities to people who are capable of making decisions that can help to change and improve the process.
d) Planning
This is one of the important roles, planning help to understand the risks and act on time when a risk becomes reality. In simple terms, how to act when an incident occurs. (Document everything).
e) Support
- Provide resources, such as budgets and time for the people, organization & team.
- Competence, making sure your team and organization have the ability to do things successfully or efficiently.
- Awareness
- Document, Document, Document everything
f) Operation
- Keep documentation to demonstrate the planned process for your organization, and justify if changes are made. This includes third parties as well.
- Documents should mention calculated risk level and also should define the risk acceptance rate.
- Risk treatment – Implement ISO 27002, Code of good practice for information security controls.
g) Performance evaluation
- Monitor, Measure, Analyse and Evaluate everything in your infrastructure. The document should contain what, how, when, and who. This means what all are monitoring, how we are monitoring when we are analyzing, and who is responsible.
- Conduct an Internal audit, it helps to understand the performance and effectiveness of your system.
- Make sure Management is aware of your audit data.
f) Improvement
Do the continuous improvement, When you find your company is non-compliant with standards, rules, or laws you must take action to improve the system and technologies. Make sure you document these as well.
The Domains Of ISO 27001
There are 18 domains in total but only 14 are audited.
- Annex A.5:Information security policies
Annex A.5.11: Policies for Information Security
Annex A.5.1.2: Review the Policies for Information Security - Annex A.6:Organisation of information security
Annex A.6.1 is responsible for the assignment of information security roles and responsibilities within the organization.
Annex A.6.2 addresses security practices for mobile gadgets and remote working. - Annex A.7:Human resource security
- Annex A.8: Asset Management
Annex A.8.1: identification of information assets according to ISMS
Annex A.8.2: information asset classification
Annex A.8.3: protection of sensitive data from unauthorized access, modification, or destruction - Annex A.9: Access Control
- Annex A.10: Cryptography
- Annex A.11: Physical and Environmental Security
Annex.A.11.1: Prevents unpermitted physical access, interference, trespass, or damage to the organization’s facility.
Annex A11.2: Protects company equipment from damage, theft, or loss. - Annex A.12: Operations Security
- Annex A.13: Communications Security
- Annex A.14: System Acquisition, Development, and Maintenance
- Annex A.15: Supplier Relations
- Annex A.16: Information Security Incident Management
- Annex A.17: Information Security Aspects of Business Continuity
- Annex A.18: Compliance
Some Additional information
Vocabulary standard:
ISO/IEC 27000, Information security management systems — Overview and vocabulary
Requirement standards:
ISO/IEC 27001, Information security management systems — Requirements
ISO/IEC 27006, Requirements for bodies providing audit and certification of information security management systems
ISO/IEC 27009, Sector-specific application of ISO/IEC 27001 — Requirements
Guideline standards:
ISO/IEC 27002, Code of practice for information security controls
ISO/IEC 27003, Information security management system implementation guidance
ISO/IEC 27004, Information security management — Measurement
ISO/IEC 27005, Information security risk management
ISO/IEC 27007, Guidelines for information security management systems auditing
ISO/IEC TR 27008, Guidelines for auditors on information security controls
ISO/IEC 27013, Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000‑1
ISO/IEC 27014, Governance of information security
ISO/IEC TR 27016, Information security management — Organizational economics
Sector-specific guideline standards:
ISO/IEC 27010, Information security management for inter-sector and inter-organizational communications
ISO/IEC 27011, Information security management guidelines for telecommunications organizations based on ISO/IEC 27002
ISO/IEC TR 27015, Information security management guidelines for financial services
ISO/IEC 27017, Code of practice for information security controls based on ISO/IEC 27002 for cloud services
ISO/IEC 27018, Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
ISO/IEC 27019, Information security management guidelines based on ISO/IEC 27002 for process control systems specific to the energy utility industry
✅Connect with me on Twitter
🤝🏽Connect with me on Linkedin
🧑🏼🤝🧑🏻 Read more post on dev.to or iCTPro.co.nz
💻 Connect with me on GitHub








